Ensuring Secure Identity Architecture with Trusted Directories

Steve Clewer
Lead Consultant, Java
Public sector organizations are responsible for processing, maintaining and protecting millions of citizens’ data. Trusted Directories make it possible to deliver the highest levels of both safety and accessibility.
In this article we discuss the features of Trusted Directories, explore their benefits as centralized systems that provide access to vetted data, and share real-world case studies demonstrating their impact.
What is a Trusted Directory?
A Trusted Directory is a curated, centralized and authoritative system or service that controls access to data—from organisations or individuals—that has been carefully vetted for legitimacy, reliability, and quality.
The Directory is considered “trusted” because it enforces security policies, maintains data integrity and ensures that only authenticated and authorised users can access certain information.
The diagram below showcases the components that typically comprise a Trusted Directory architecture:
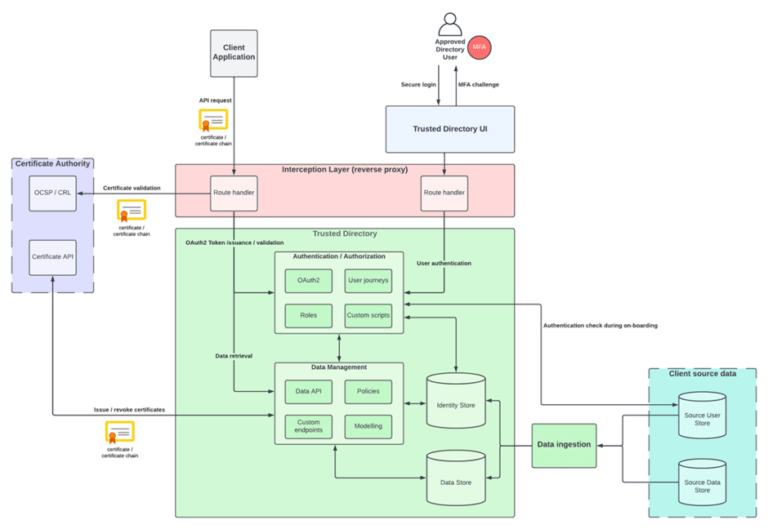
Features of Trusted Directories
On-boarding process: All actors are on-boarded through a restricted, vetted process. This involves verifying client sources of truth, such as organization data and user details like email addresses. Data ingestion can occur through full-scale, one-step migration or lazy user migration.
Identity verification: In some cases, this may be provided via a third-party external Identity Provider (IdP), such as a government-backed identity system. The IdP performs identity checks a priori and authentication to the IdP is part of the on-boarding.
Certificate issuance: Authorised users obtain certificates issued by a dedicated Certificate Authority (CA). Transport certificates allow access to the Directory data via APIs, which are protected by CA OCSP/CRL validation enforced at the entry point. This is usually some kind of API request interception layer. Signing certificates allow signing of request payloads, typically JWT structures, associated with the system. Public keys are exposed via the Directory JWKS endpoint for third-party verification.
OAuth2/OIDC integration: Trust is augmented by OAuth2/OIDC short-lived token generation. Access can be further controlled with access token scopes, and OAuth2 clients can be created specifically for each organisation. Client-certificate binding (RFC-8705) may be used to restrict access token generation.
User interface: Often, a dedicated UI facilitates onboarding and enables users to manipulate their associated data within the directory.
Multi-factor authentication: MFA is often required by users, in addition to login credentials, to further augment secure login.
Trusted Directories play a crucial role in enhancing security and compliance. By implementing a Trusted Directory, organizations can ensure data integrity, meet regulatory requirements, and provide a secure environment for managing sensitive information. In short, they’re essential for managing complex ecosystems and ensuring secure access to critical services.
You can learn more about Ensono’s Identity and Access Management solutions here.
Social Share
Don't miss the latest from Ensono
Keep up with Ensono
Innovation never stops, and we support you at every stage. From infrastructure-as-a-service advances to upcoming webinars, explore our news here.
Blog Post | April 14, 2025 | Technology trends
IBM z17: The Age of AI on The Mainframe Has Arrived. Are You Ready to Meet It?
Blog Post | March 19, 2025 | Industry trends
The Hidden Costs of Legacy Data Centers – Are You Paying More Than You Realize?
Blog Post | March 7, 2025 | Industry trends