MaMi macOS Malware: What You Need to Know

Joe Reyes
Senior Manager, Security
New macOS malware was recently discovered “in the wild.” Named MaMi, this unsophisticated malware can seize DNS settings, with address changes 82.163.143.172 and 82.163.142.174 remaining persistent – even after removing these entries.
Mami can also execute code, download/upload files, persist as a launch item, generate simulated mouse events, and screenshot capture any infected Macs. Attackers can steal credentials and inject ads.
Not every antivirus can locate MaMi as of yet. As a precaution, we are recommending that our clients ensure no machines are infected by running regular scans and updating definitions. Attack vectors, which enable hackers to exploit system vulnerabilities, are currently unknown.
There are ways you can check if your computer is infected
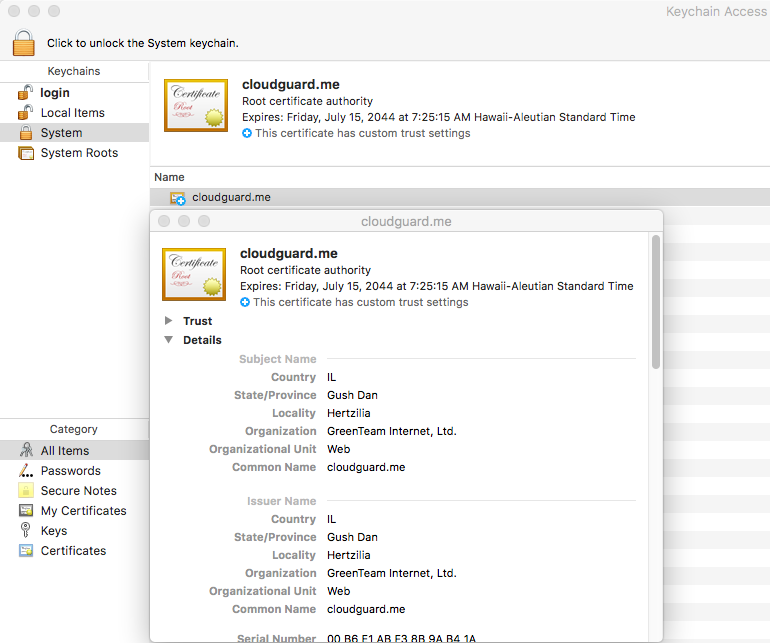
1. Check the System settings in Keychain Access that an unwanted certificate was installed, similar to the sample below:
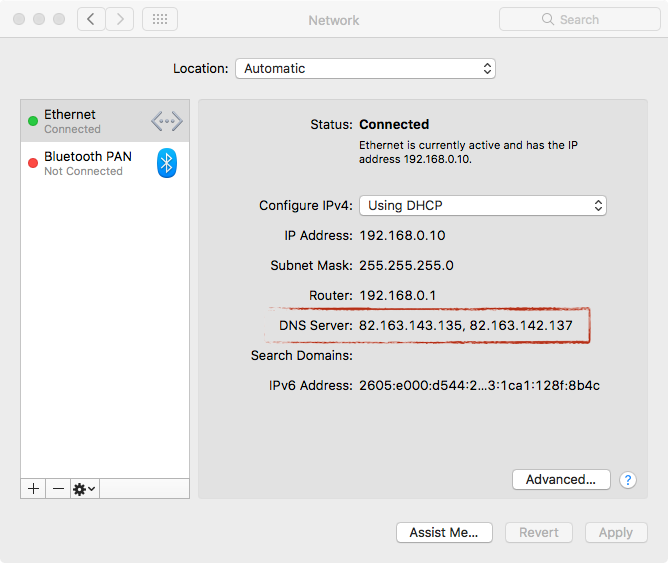
2. Check if your DNS Server settings have been altered. See an example of a compromised host below:
What to do if your system is infected
Wipe the drive and re-install Mac OS. If an OS refresh isn’t possible, do the following:
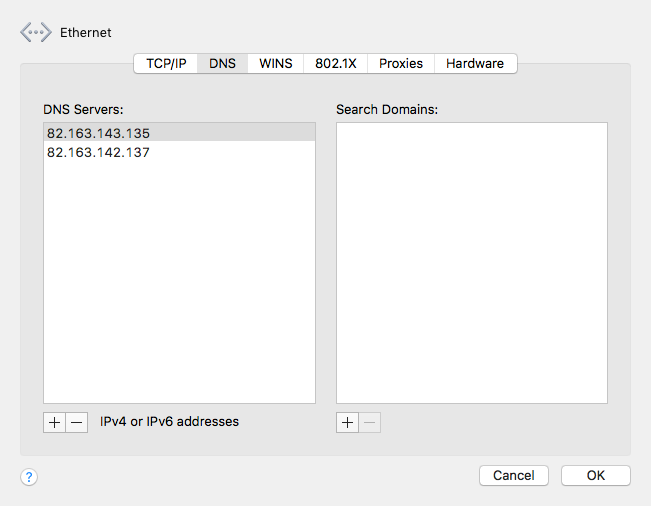
- Change your DNS Settings
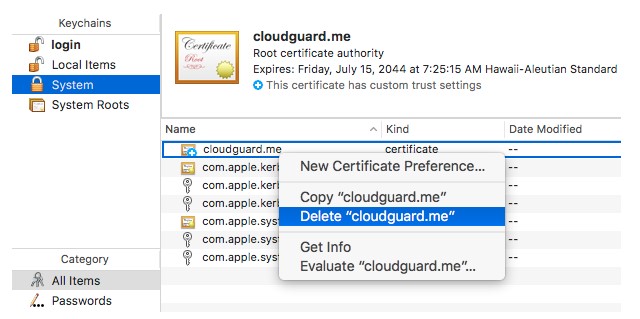
- Remove the rogue root certificate
These steps are necessary to ensuring your machines and data are safe in the age of bad actors and compromised cybersecurity.
Social Share
Don't miss the latest from Ensono
Keep up with Ensono
Innovation never stops, and we support you at every stage. From infrastructure-as-a-service advances to upcoming webinars, explore our news here.
Blog Post | April 16, 2025 | Industry trends
Closing the Cloud Skills Gap with Engineering Talent that Flexes with You
Blog Post | April 8, 2025 | Technology trends
IBM z17: The Age of AI on The Mainframe Has Arrived. Are You Ready to Meet It?
Blog Post | March 28, 2025 | Inside Ensono